Finally, here we are — the conclusion of my honeypot experiment. My original intention was to aim for a total of one million logged attacks, at which point I would shut down the honeypot. However, schoolwork fully occupied my attention for a brief period. Thus, I considered it a better idea to continue collecting data until I could find time to perform a proper analysis. That time is now, and instead of blocking traffic upon “only” the millionth attack, the Elastic dashboard looks like this:
The million-attack target was surpassed by a significant margin. But, without further ado, let’s examine the results.
Preliminary Information
All bait services were exposed to the Internet on 19 January 2022 at 3:00 PM PST. I restricted all traffic on my VPC to my IP address on 09 February 2022 at 6:00 PM PST. Thus, services were exposed for external attack for 21 days and 3 hours.
In that time, over 1,566,300 attacks were recorded by the following honeypots:
- Adbhoney
- Ciscoasa
- Citrixhoneypot
- Conpot
- Cowrie
- Ddospot
- Dicompot
- Dionaea
- Elasticpot
- Endlessh
- Glutton
- Heralding
- Hellpot
- Honeypots
- Honeypy
- Honeysap
- Honeytrap
- Ipphoney
- Log4pot
- Mailoney
- Medpot
- Rdpy
- Redishoneypot
- Snare
- Tanner
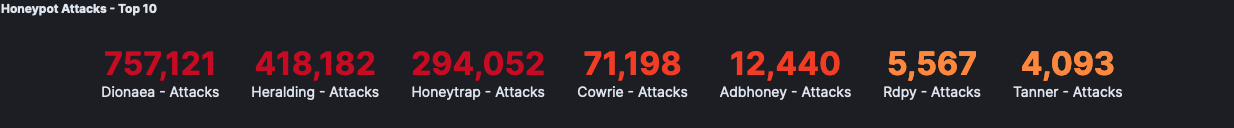
Setup was automated by Telekom’s T-POT. Since Dionaea (757,121), Heralding (418,182), Honeytrap (294,052), Cowrie (71,204), Adbhoney (12,440), Rdpy (5,567), and Tanner (4,093) logged the vast majority of the attacks, I will maintain focus on them for the most part.
The honeypot was hosted for the duration of its uptime on a Google Cloud instance in The Dalles, Oregon on us-west1. The host OS was Debian 10 and firewall rules permitted ports UDP and TCP 1 to 64000 ingress access from any IP address. This honeypot was not intended to appear as a legitimate target for hackers to manually compromise, but rather a target for malicious bots. As could be seen on Shodan (screenshot below), the host was undisputably a honeypot. Tip: click or tap the image to zoom in.
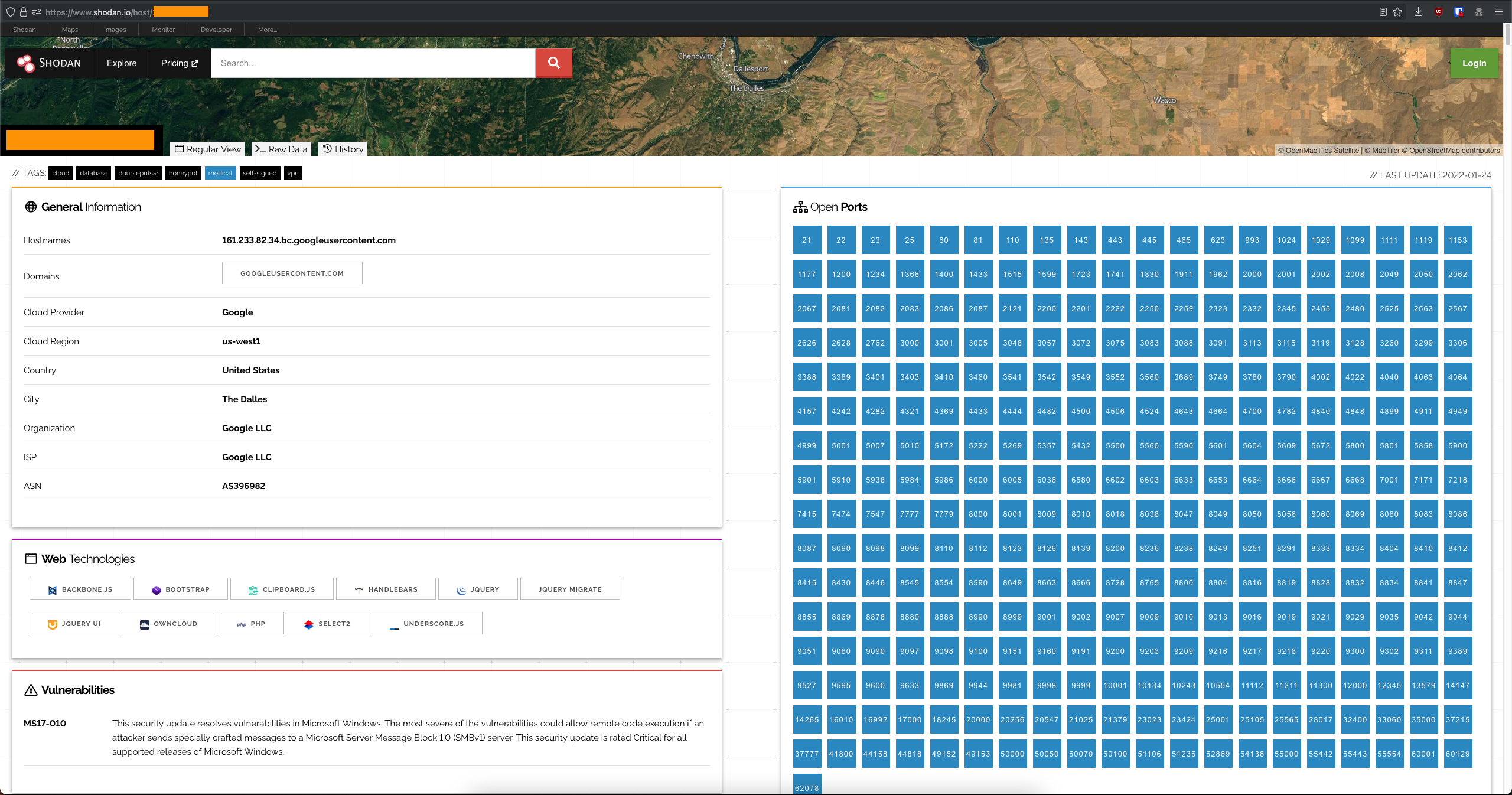
No legitimate host would have that many open ports, and if so… Well, respectfully, the sysadmin in charge should consider re-evaluating their security policy.
All binaries examined in previous sections of this series have been sourced from the honeypots executed here within the aforementioned timeframe.
Data
Most Popular Attack Vectors
By far, the most common type of attack was brute-forcing common credential sets against services that support login, especially SSH, VNC, RDP, and FTP; I suppose naive attacks are to be expected. Let’s take a look at which usernames and passwords were used. T-POT uses Elastic to generate useful word clouds of these points of data.
Usernames
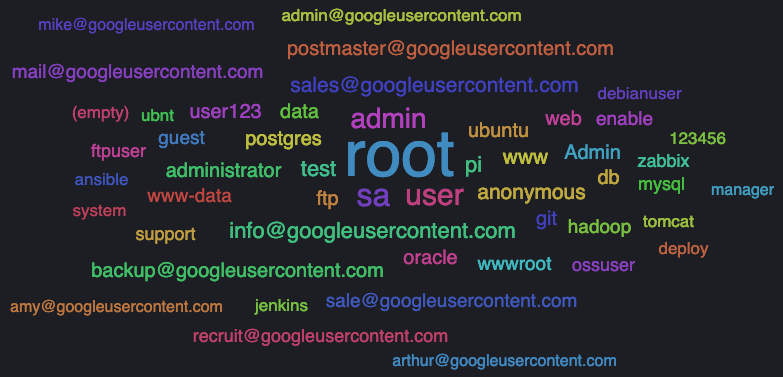
Note that not all usernames are shown here. Download the full dataset here. The top five usernames attempted across all services were:
root— 6,222 attemptssa— 711 attemptsuser— 546 attemptsadmin— 412 attemptstest— 145 attempts
All of these, especially root, seem pretty reasonable to me.
Passwords

Note that, as with the usernames, not all passwords are shown here either. Download the full dataset here. The top five passwords attempted across all services were:
Password— 600 attempts123456— 431 attempts1— 398 attempts- empty/no password — 353 attempts
Passw0rd— 292 attempts
Again, all quite reasonable. Here are some that are perhaps less than reasonable:
raspberryraspberry993311— 55 attempts; see this post for more information^_^$$wanniMaBI:: 1433 vl— 40 attempts; what?
Always set unique, secure passwords! The bots that targeted my honeypot take advantage of those who want the convenience of only remembering 123456 as their password.
Origins of Attack
Things get particularly interesting here — see the breakdown of attacks by country below. Note that even though an attack comes from an ASN located within certain borders, the attacker(s) may very well have routed their traffic in a complex manner to hide their identities. Thus, attacks that originate from the United States but route through Utrecht with a VPN will, of course, appear to be Dutch attacks instead.
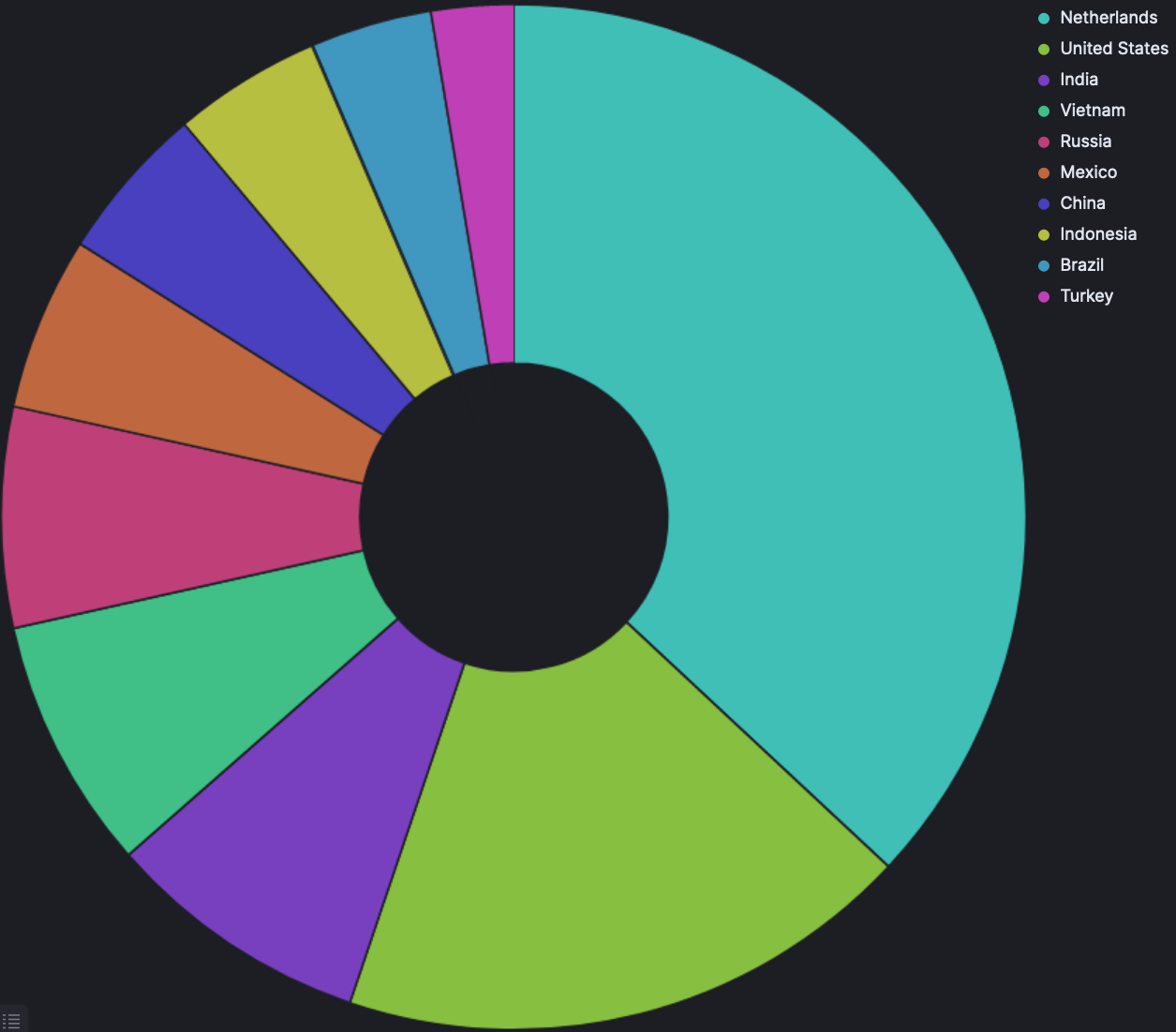
Numerical breakdown in terms of attacks by country:
- Netherlands: 415,771
- United States: 205,221
- India: 94,108
- Vietnam: 89,762
- Russia: 78,176
- Mexico: 61,626
- China: 55,720
- Indonesia: 52,440
- Brazil: 43,013
- Turkey: 29,550
Damned Dutch and their… cyber criminals? I did not expect these results at all. A map of estimated attack origins is shown below, which can also be downloaded here.
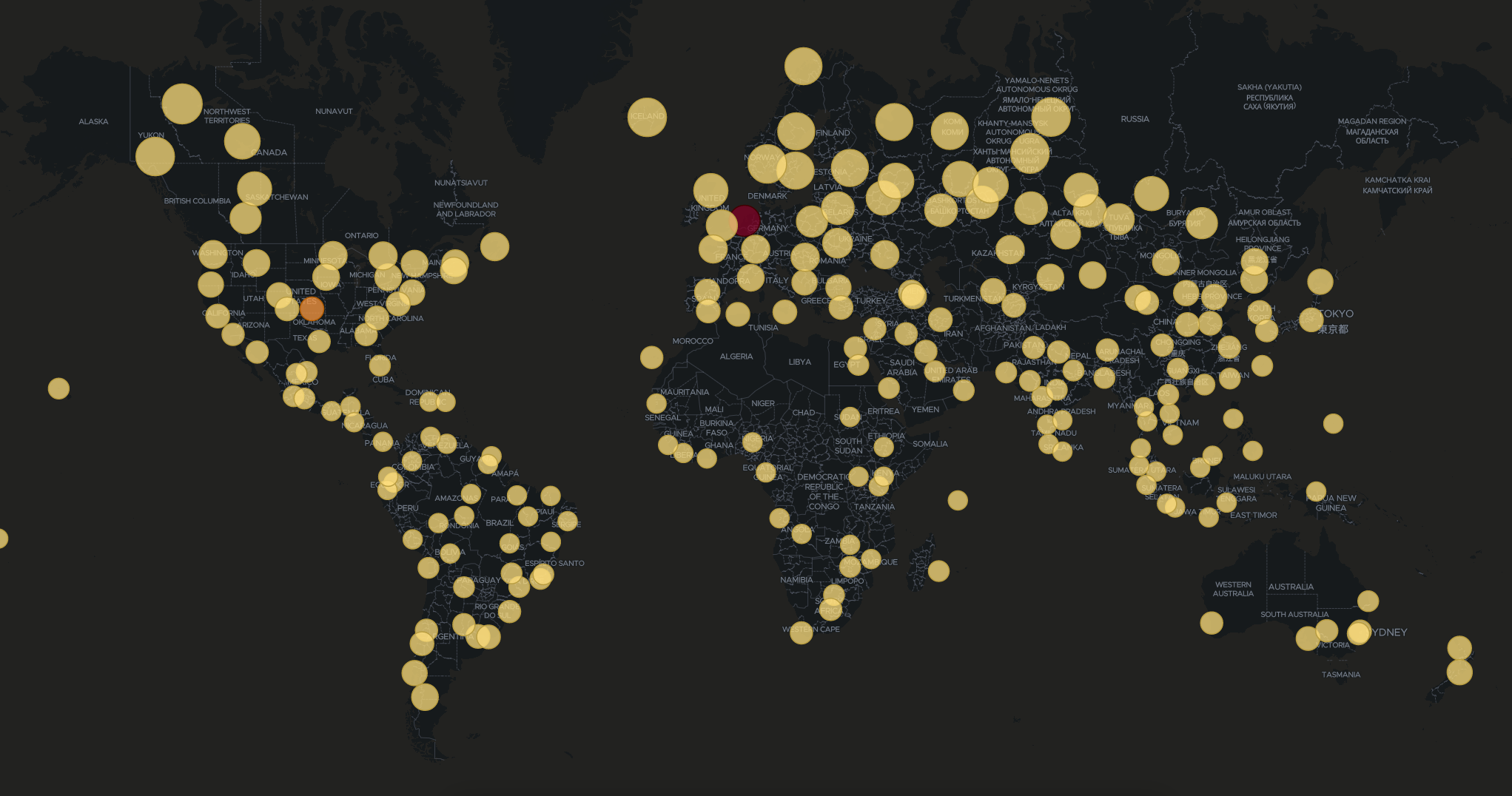
Here is more information:
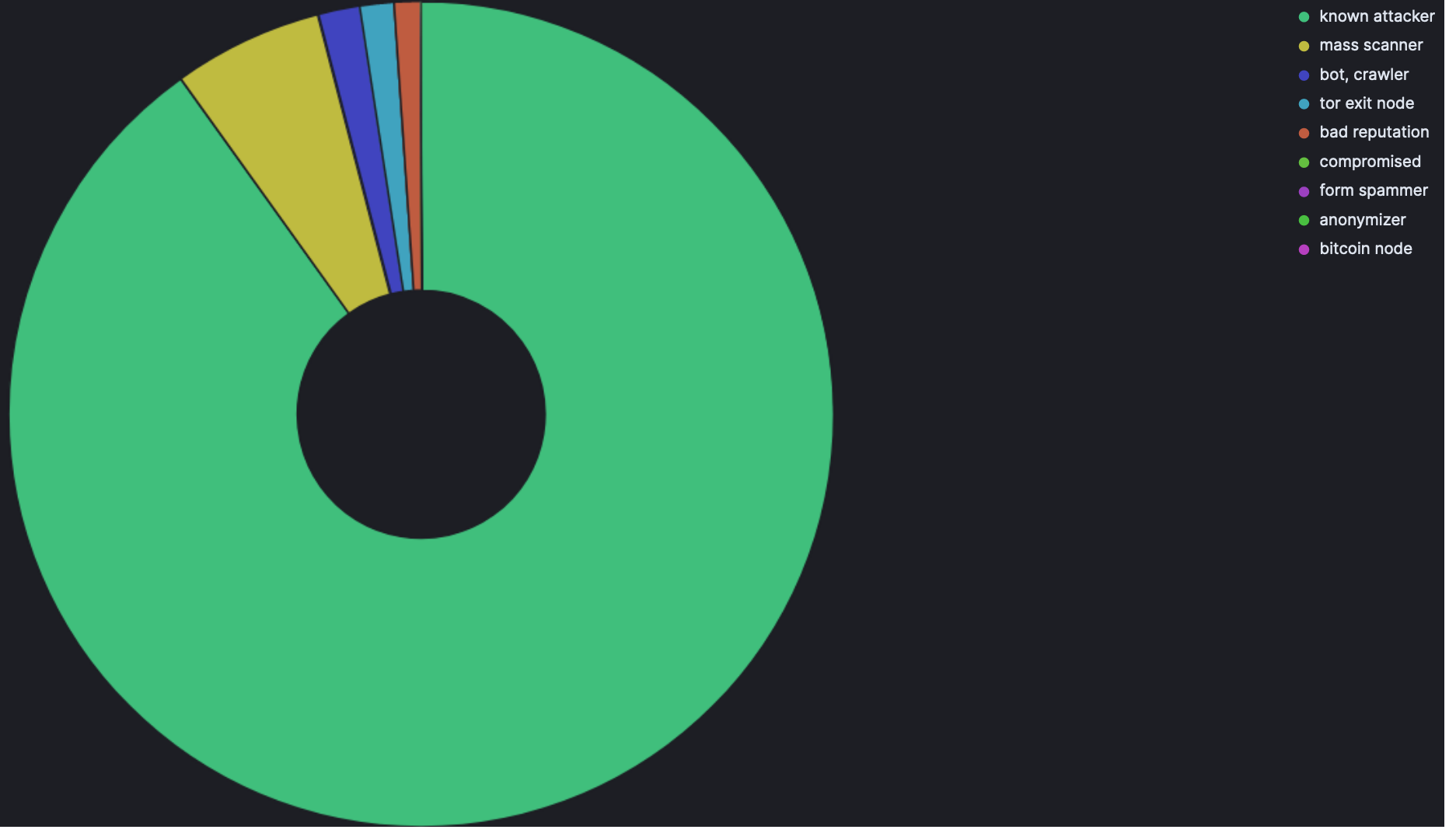
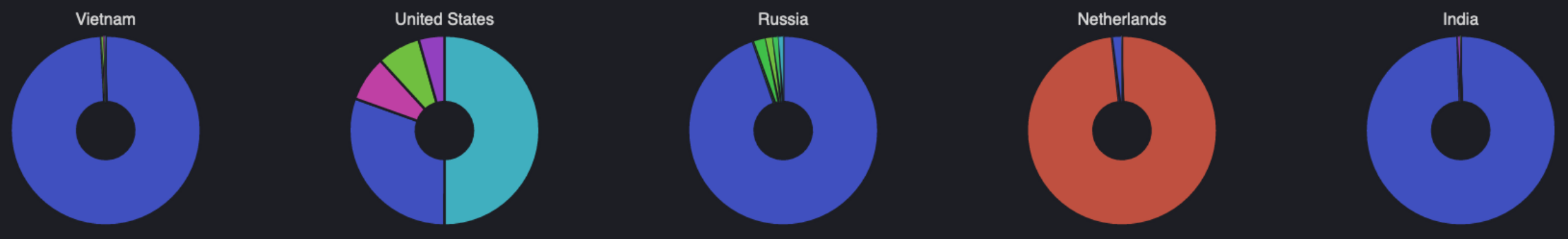
Here is a list of the most common attack origins by IP address:
185.232.52.40— 395,126 attacks193.169.254.17— 21,041 attacks159.89.48.65— 13,889 attacks189.84.186.154— 12,810 attacks103.103.175.121— 11,046 attacks202.88.237.202— 11,043 attacks200.23.18.185— 11,042 attacks103.151.218.73— 11,041 attacks163.53.180.248— 11,041 attacks175.111.4.204— 11,039 attacks
Curiously, as of the time of publication, I appear to be one of the only reporters of 185.232.52.40 on VirusTotal; surprising, given the volume of attacks.
And, finally, here is a list of the top ten attacks by the ASN the origin address belongs to:
- 200313 (“Internet It Company Inc”): 395,229 attacks
- 7552 (“Viettel Group”): 50,968 attacks
- 14061 (“DigitalOcean, LLC”): 27,776 attacks
- 8151 (“Uninet S.A. de C.V.”): 26,367 attacks
- 7713 (“PT Telekomunikasi Indonesia”): 25,264 attacks
- 4134 (“No.31,Jin-rong Street”): 25,247 attacks
- 45899 (“VNPT Corp”): 22,694 attacks
- 197226 (“sprint S.A.”): 21,055 attacks
- 8048 (“CANTV Servicios, Venezuela”): 19,010 attacks
- 8452 (“TE-AS”): 16,526 attacks
Attacks
I have included several charts below. Patterns can easily be seen, especially relating to activity from the Netherlands.
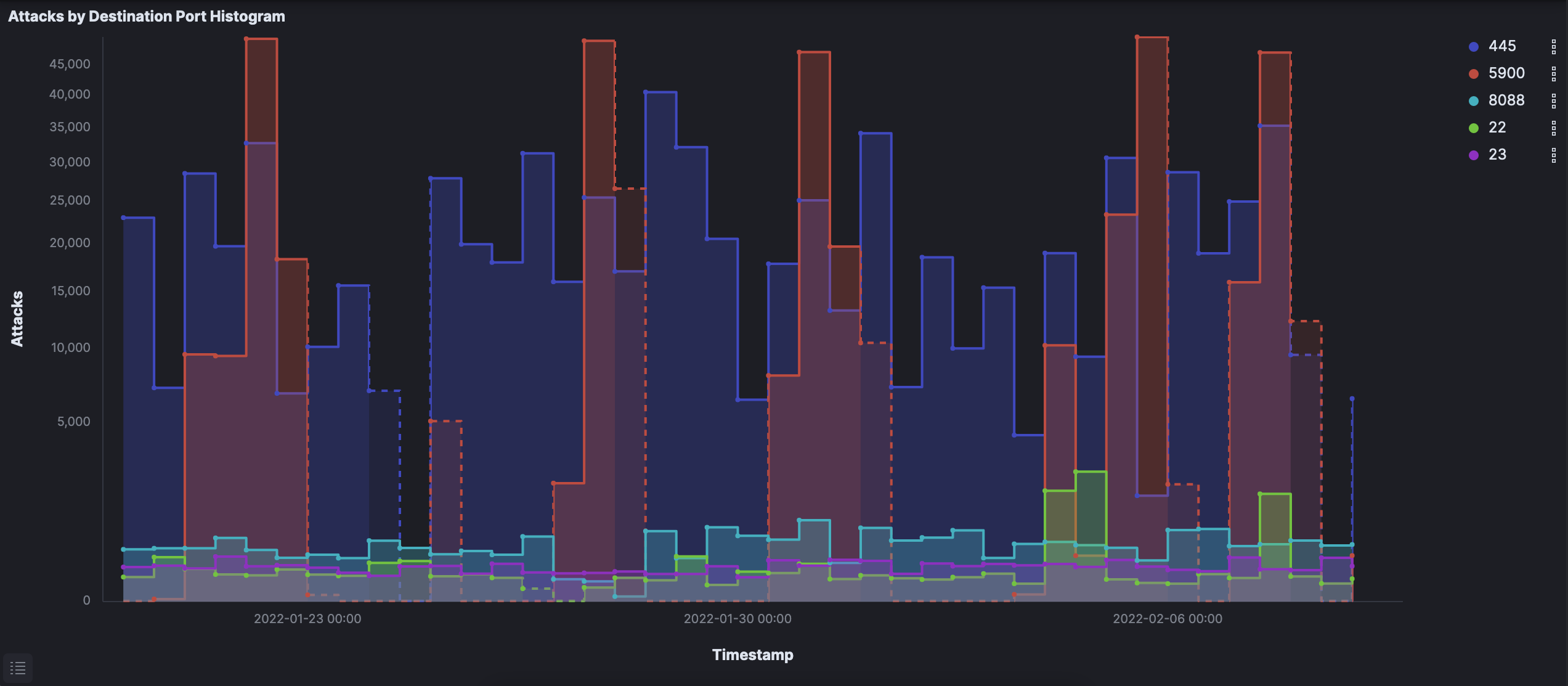
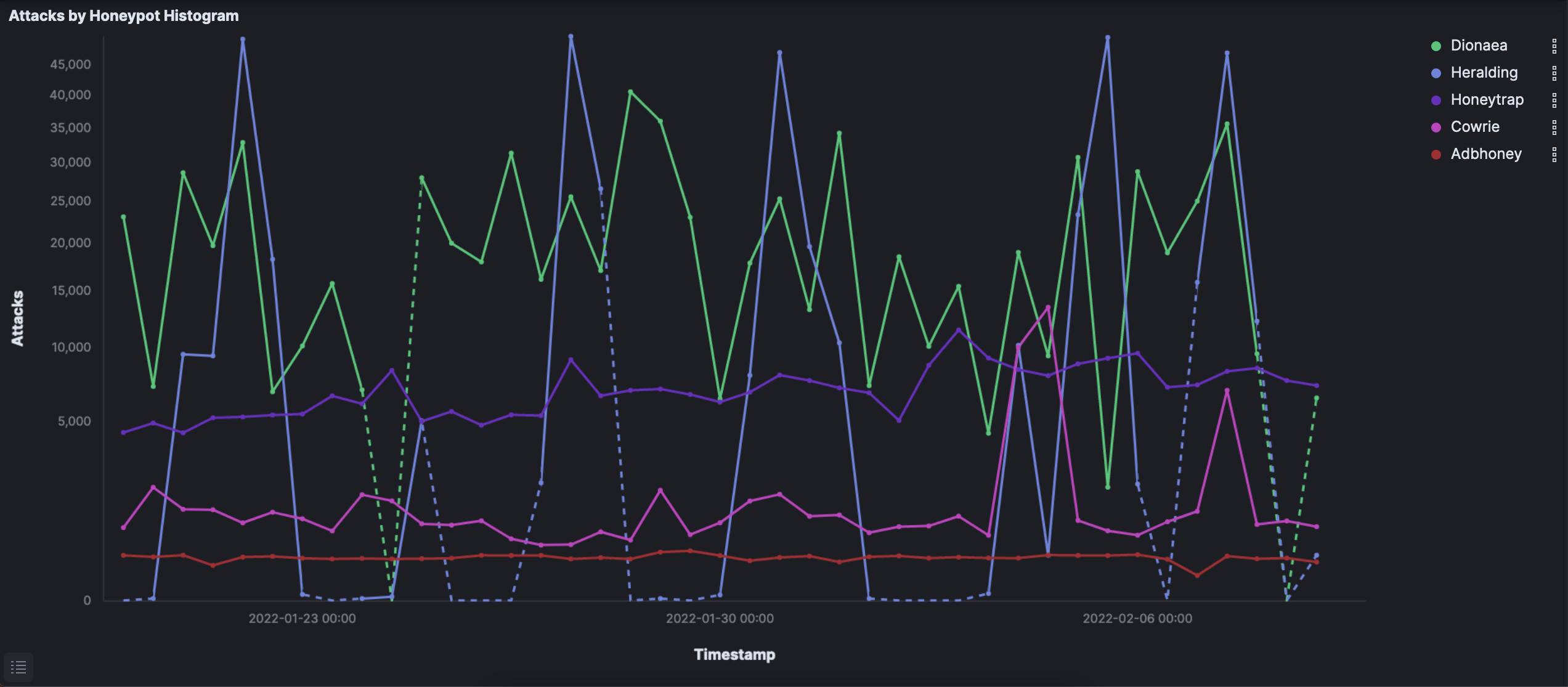
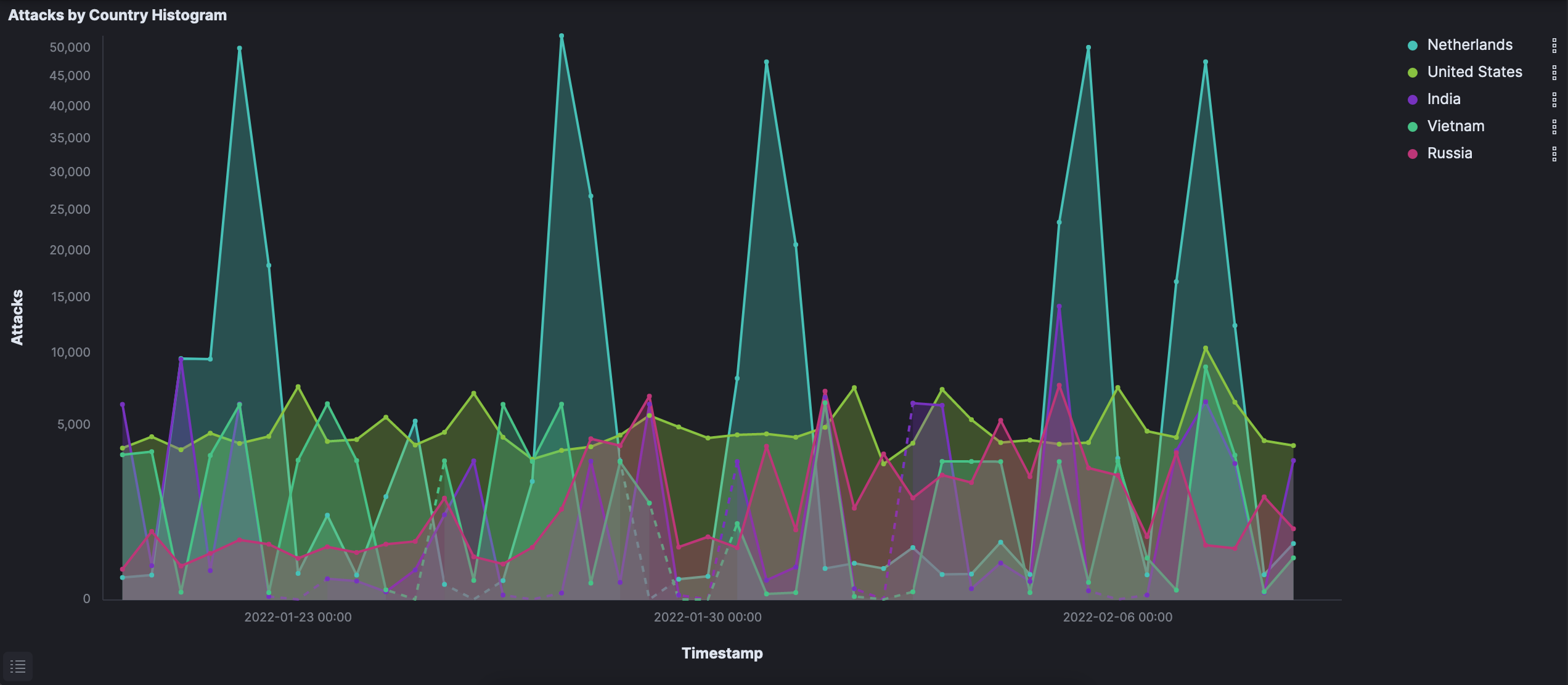
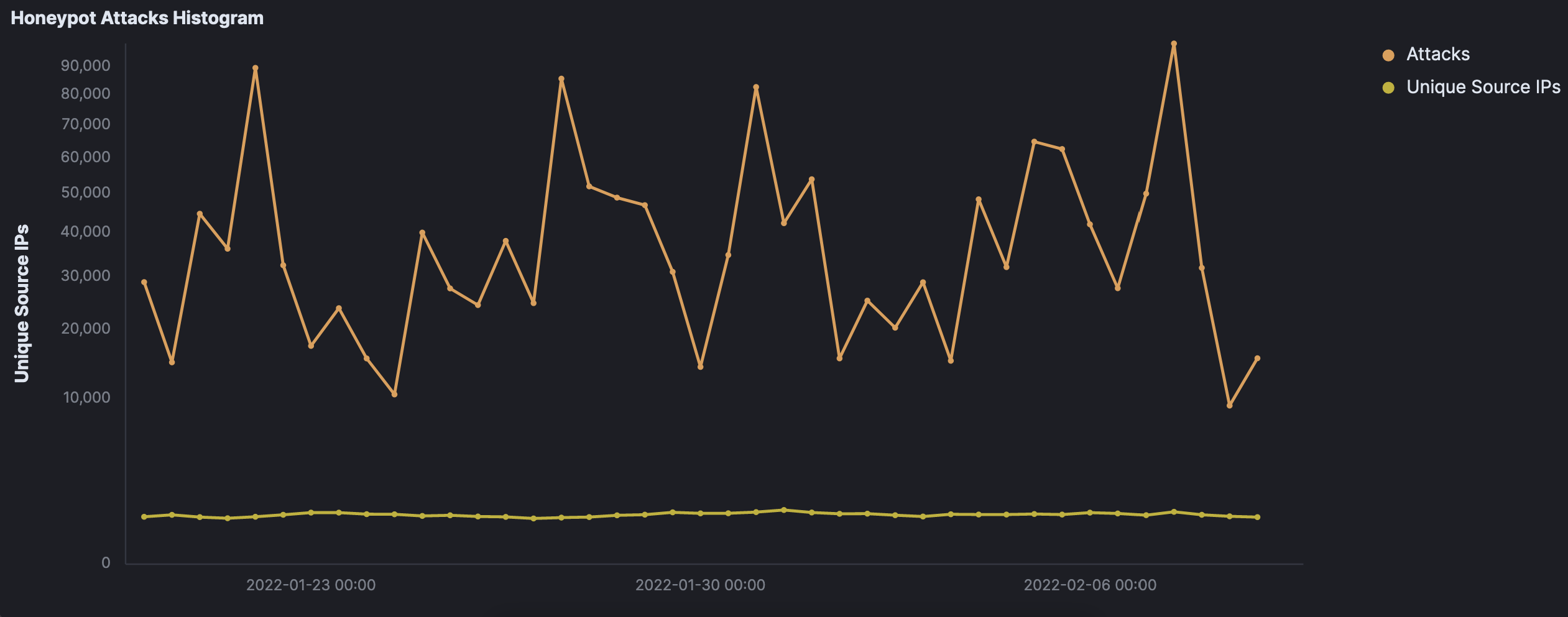
Attempted brute-force attacks towards port 5900 (VNC) by the Netherlands remain the most significant pattern overall in terms of scope — the Netherlands composed over one-third of all 1.5 million attacks on its own. Of particular note is the measurable spikes of activity during those attacks. In all, just under 400,000 attempts were made by what I assume is the same bot or group of bots routing traffic through the Netherlands.
Brief Conclusions
So, what can we learn here? The most significant point to me is that the vast majority of automated attacks that targeted me used naive methods. My findings here only serve to reinforce the idea that the most dangerous elements in computer security are us. Attackers here were not abusing zero-day flaws, nor using sophisticated methodologies.
Instead, bots were used to perform mass reconnaissance, searching for low-hanging security fruit, namely default passwords. The attackers were looking for those of us who habitually neglect to employ comprehensive initial security configurations. Those of us who put off applying security patches for years (the most common exploit attempt by far was CVE-2006-2369). Those of us who leave all of our services exposed to the Internet at all times unnecessarily. Ransomware was deployed nearly 100 times, but it wasn’t novel technology; no, it was mainly WannaCry, patched by Microsoft in 2017.
As a security community, we can certainly do better. These attacks wouldn’t occur if they weren’t successful at times. Even the most basic security policy would mitigate the majority, if not all of the attacks I received. Let’s make sure we change our passwords, use firewalls — they exist for a reason — and patch our software to keep our environments safe.